Software
DOMDig
DOM XSS scanner for Single Page Applications.
Github
HTCAP
htcap is a web application scanner able to crawl single page application (SPA) in a recursive manner by intercepting ajax calls and DOM changes.
It also features a small but powerful framework to quickly develop custom fuzzers with less than 60 lines of python.
Github
HTCRAWL
Nodejs module build on top of Puppetteer for crawling, scraping and scanning of single page applications (SPA).
Github
Vulnerabilities
Mac OS X GateKeeper bypass
On MacOS X version <= 10.14.5 (at time of writing) it is possible to easily bypass Gatekeeper in order to execute untrusted code without any warning or user's explicit permission.
CVE: CVE-2019-8656
TorMoil – Deanonymize Tor Browser Users
Tor Browser version 7.0.8, and probably prior, for Mac OS X and Linux, is affected by an information disclosure vulnerability that leads to full de-anonymization of website visitors using just a single html tag (no js)
CVE: CVE-2017-16541
Squirrelmail Remote Code Execution
Squirrelmail version <= 1.4.22 is vulnerable to a remote code execution vulnerability (authenticated).
CVE:
CVE-2017-7692
Misc.
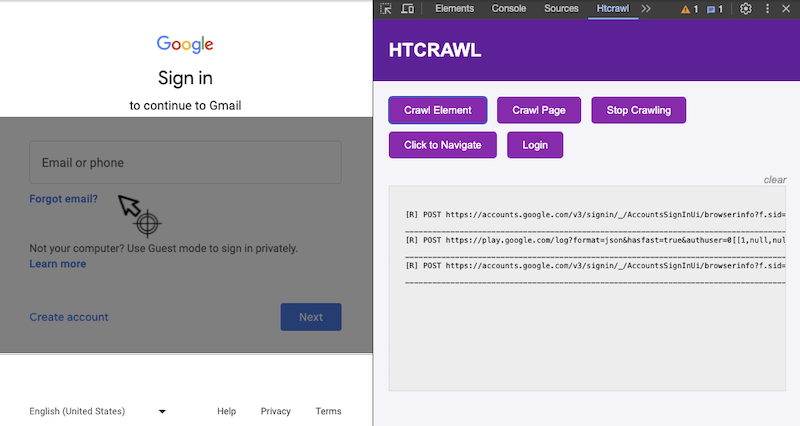
Htcrawl goes interactive
12 November 2023
The new release of Htcrawl includes a chrome extension that allows the user to crawl SPAs interactively!
It implements a small GUI (as a devtool panel) allowing the user to perform several actions on the page like
selecting the DOM element to crawl or perfom manual logins.
It also features a CLI to run the crawler without writing code.
$ npx htcrawl tools crawler https://gmail.com
Via code, the UI can be easily personalised:
const customUI = {
extensionPath: __dirname + '/chrome-extension',
UIMethods: UI => { // Evaluated in the context of the page
UI.start = () => {
UI.dispatch("start")
}
},
events: { // Events triggered by 'UI.dispatch()' from the page context
start: async e => {
await crawler.start();
// Sent a message to the browser extension
crawler.sendToUI("DONE")
},
}
}
New project: Burp DOM Scanner
12 April 2023
It's a Burp Suite's extension that acts as GUI for Domdig
It allows for recursive crawling and scanning of Single Page Applications directly from Burp.
DOMDig version 1.0.0 released!
18 October 2019
DOMDig is a DOM XSS scanner based on htcrawl.
During the crawling process, XSS payloads are put into input fields and their execution is tracked in order to find injection points and the related URL modifications.
Github
HTCAP can now crawl gmail
14 October 2019
With the new updates, htcap is able to automatically login into gmail and crawl the application.
During this video more than 3000 AJAX request have been detected and acquired.
It has a crawling timeout that prevents htcap from running for too long (in this case 2 hours per page) and it has been manually stopped after ~3 hours, but, theoretically, it can run for days on complex apps like gmail.
Github
Update: MacOS X Gatekeeper bypass Fixed!
22 Jul 2019
Apple finally fixed it! https://support.apple.com/en-gb/HT210348
The following CVE has been assigned: CVE-2019-8656
MacOS X Gatekeeper bypass
24 May 2019
Easy and reliable way to bypass Gatekeeper on MacOS X. It seems that Apple won't release any patch or solution for this ;(
Some press: Wired
| The Hacker News
| Threat Post
| Bleepingcomputer
Proudly introducing HTCRAWL
23 February 2019
HTCRAWL, the crawling engine used by HTCAP, is now available as nodejs module!
With HTCRAWL you can easly crawl, scan and scrape single page applications or roll your own DOM-XSS scanner with less than 60 lines of code.
Github
const htcrawl = require('htcrawl');
// Get instance of Crawler class
const crawler = await htcrawl.launch("https://htcrawl.org");
// Print out the url of ajax calls
crawler.on("xhr", e => {
console.log("XHR to " + e.params.request.url);
});
// Start crawling!
crawler.start();
Proudly sharing the video of my TEDx speech
11 December 2019
I'm proud to share the video of my speech at TEDx Treviso. The speech is in italian and has not yet been translated by the TED staff.
HTCAP now features its own http fuzzers
7 January 2019
HTCAP can now discover SQLi, XSS command injection, file inclusion and more without the use of external tools.
A small but powerful framework to develop custom fuzzers has been added on top of HTCAP.
More infos here
def fuzz(self):
vulnerabilities = []
# Initialize mutations iterator.
# A mutation is an object that holds the original request with a parameter replaced with a payload
mutations = self.get_mutations(self.request, payloads)
for m in mutations:
try:
resp = m.send()
except Exception as e:
self.sprint("Error: %s" % e)
continue
if not resp.body:
continue
if self.is_vulnerable(resp.body):
vulnerabilities.append(str(m))
mutations.next_parameter()
return vulnerabilities
HTCAP version 1.1 is out!
14 November 2018
Goodbye phantomjs and thanks for the great job you did!! And.. welcome Puppetteer!!
Now HTCAP uses headless chrome as browser engine with full support for ECMA script 6.
The crawling engine has been rewritten from scratch to take advantage of async/await features.
Github
TorMoil: all the details revealed
10 September 2018
I'm finally proud to reveal all the details about TorMoil. The Firefox team finally fixed the vulnerability that leads to TorMoil on Tor Browser.
Plus, another similar vulnerability exists on Windows but it needs user interaction to be exploited: details here
TorMoil: TorBrowser unspecified critical security vulnerability
30 October 2017
TorBrowser version 7.0.8, and probably prior,for Mac OS X and Linux, is affected by an unspecified critical security issue.
According to the Tor Project, further details will be released in the near future.
Some press: The Hacker News
| The Inquirer
| Threat Post
| Bleepingcomputer
Mac OS X Local Javascript Quarantine Bypass
27 September 2017
Mac OS X contains a vulnerability that allows the bypass of the Apple Quarantine and the execution of arbitrary Javascript code without restrictions.
The vulnerability was trivial as hell and Apple choosed to SILENTLY FIX it by removing the vulnerable component from the operating system.. Come on Apple, don't be too ashamed of your stupid mistakes.
Some press: Bleepingcomputer
| Security week
Update: 22 July 2019
I accidentally discovered that Apple documented this fix later in November 2017 (https://support.apple.com/en-us/HT208144). The following CVE was assigned: CVE-2017-13819
Squirrelmail Remote Code Execution
19 April 2017
Squirrelmail version <= 1.4.22 is vulnerable to a remote code execution vulnerability because it fails to sanitize a string before passing it to a popen call.
It's possible to exploit this vulnerability to execute arbitrary shell commands on the remote server.
Some press: The Register
| Threat Post
| Helpnet Security
Microsoft Remote Desktop Client for Mac Remote Code Execution
7 December 2016
A vulnerability exists in Microsoft Remote Desktop for Mac that allows a remote attacker to execute arbitrary code on the target machine.
Htcap beta 1.0, now it’s a vulnerability scanner
26 February 2016
Htcap is a web application scanner able to crawl single page application (SPA) in a recursive manner by intercepting ajax calls and DOM changes. Github
Symphony CMS Multiple Vulnerabilities
8 February 2016
The contentAjaxQuery class suffers from a SQL-Injection vulnerability because the request parameter "query" is used to build a sql query without beeing properly sanitized.
ProjectSend multiple vulnerabilities
26 January 2016
ProjectSend (previously cFTP) suffers from multiple vulnerabilities
Lychee remote code execution
15 April 2015
Lychee version 2.7.1 and probably below suffers from remote code execution vulnerability.